This is the fourth installment in a series of articles delving into cybersecurity challenges facing South Korea and the world, and global efforts to tide them over. ― Ed.
With outmoded fighter jets, warships and tanks and underfed soldiers, North Korea could hardly be seen as a military power. But through its dogged pursuit of nuclear arms and long-range missiles it has built itself into a force to be reckoned with.
Beyond the traditional military domain, the communist state has also sought to become a formidable player in cyberspace with a sizable portion of its scarce defense resources dedicated to training “cyberwarriors” and boosting online combat capabilities.
“North Korea is pursuing cyberwarfare capabilities as a form of asymmetric warfare to marginalize specific U.S.-ROK (Republic of Korea) military strengths,” said Michael Raska, a security expert at Nanyang Technological University in Singapore.
“North Korea is adaptive. They constantly study how U.S.-ROK forces fight, and develop capabilities that leverage their strengths against South Korean weaknesses. Raising cyberwarfare capabilities will therefore be an increasingly important strategic priority for them.”
 |
North Korean students work in a computer lab at Kim Il-sung University in Pyongyang. (AP-Yonhap) |
A string of cyberattacks carried out by the North in recent years has galvanized the South into establishing a cyberwarfare command; cultivating hacking experts; and seeking legal and institutional tools, and international cooperation to improve its cybersecurity.
Experts say that Seoul should map out a more comprehensive interservice strategy to counter growing cyberthreats that could possibly paralyze the nation’s financial, social and military infrastructure at a relatively small cost from far-flung, difficult to trace locations.
N.K. focusing on cyberwarfare
With its debilitated economy, Pyongyang has sought the most cost-effective ways to ensure its national security in the face of its more affluent, well-equipped adversaries: South Korea and the U.S.
Recognizing that it would not be successful in a conventional form of warfare against its allied enemies, the North has pushed to develop its so-called “asymmetric” capabilities such as weapons of mass destruction including nuclear arms, long-range ballistic missiles and special commandos.
Cyberwarfare capabilities have also become an integral part of the North’s asymmetric military strategies.
“With the use of cyberwarfare operatives, Pyongyang could achieve various critical outcomes at a low cost. It could cause serious social confusion by launching cyberattacks to disrupt South Korea’s infrastructure management networks,” said Lee Dong-hoon, a professor at Korea University’s Graduate School of Information Security.
“It could also foster division among South Koreans and foment social instability though some sort of psychological warfare in cyberspace.”
The North has also utilized its cybercapabilities to gain economic benefits, according to Jang Se-yul, a North Korean defector and former officer of North Korea’s electronic warfare unit.
“Many North Korean soldiers are deployed abroad and break into foreign networking systems to glean intelligence on economic affairs as well. In this way, the cyberwarriors can help the North attract foreign investment and rake in hard foreign currency,” Jang told The Korea Herald.
The North is estimated to have nearly 6,000 cyberwarfare troops, most of whom work for a series of cybersecurity units under the General Bureau of Reconnaissance, the North’s premier military intelligence agency.
Seoul blames the GBR for a spate of cyberattacks in recent years and deadly provocations including the torpedo attack on the South Korean corvette Cheonan in March 2010 that killed 46 sailors. The North denies responsibility for the attack.
The number of cyberwarfare troops in the North has nearly doubled over the last two years, military sources believe. Of the total, some 1,200 troops including those deployed overseas are thought to be professional hackers. The figure is substantially higher than the estimated 500 personnel of South Korea’s Cyberwarfare Command.
The North has systematically nurtured cyberelites. Jang, who attended Mirim University in Pyongyang from 1987-92, recalled how much the reclusive state stressed the importance of cyberwarfare.
“The North has quite a long history of cyberwarfare education and training. It started in the mid-1980s. As the nation invests a lot into nurturing specialists, students are also given chances to go abroad to receive training from foreign universities (in China and Russia),” he said.
According to defectors and reports, the North selects cybersavvy students from across the country, and sends them to Geumseong Middle School in Pyongyang to give them intensive cybersecurity training.
They are then sent to Kim Il-sung Military University, Command Automation University, Kim Chaek University of Technology or Moranbong University for further education. Upon graduation, they become elite cyberwarfare officers.
Established in 1986, CAU under the North’s Ministry of the People’s Armed Forces is believed to produce more than 100 cyberwafare experts each year. The GBR established Moranbong University in the 1990s to cultivate hacking experts.
Cyberwarfare organs, attacks
The North’s cyberwarfare organs belong to the General Bureau of Reconnaissance or the General Staff of the North Korean People’s Army. The two entities are under the country’s powerful National Defense Commission.
Under the GBR is Unit 121, which is tasked with penetrating enemy computer networks to secure confidential documents or spread viruses. The GBR was established in 2009 after the reconnaissance division of the Ministry of the People’s Armed Forces was merged with the operations division and Office No. 35 of the ruling Workers’ Party.
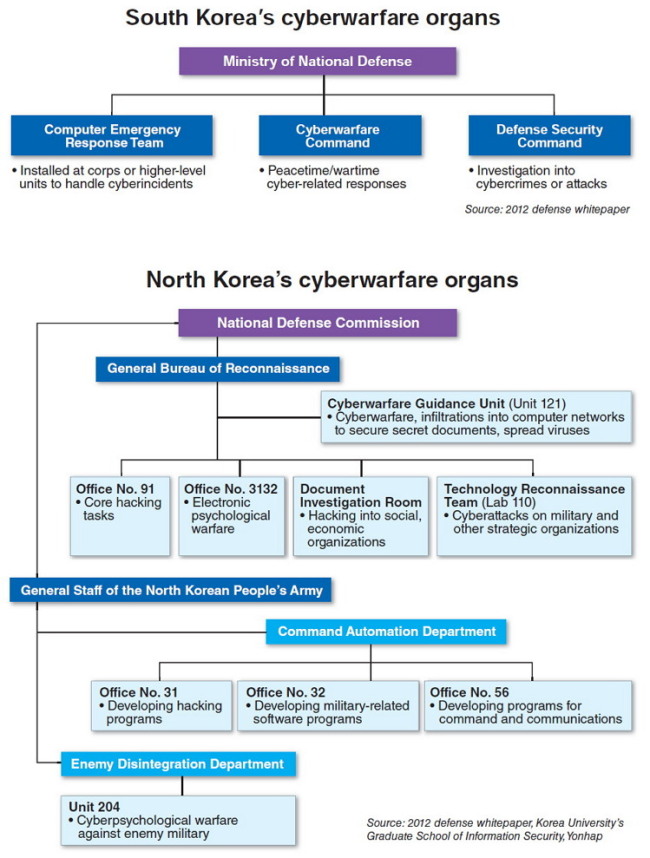
Also under the GBR are Offices Nos. 91 and 3132, in charge of hacking missions and electronic psychological warfare, respectively. Lab 110 of the GBR is tasked with launching cyberattacks on the enemy’s military or other strategic installations.
The Command Automation Department belongs to the General Staff of the military. It has Offices Nos. 31, 32 and 56, in charge of developing hacking programs, military-related software and programs for command and communications, respectively.
Also attached to the General Staff is the Enemy Disintegration Department, which includes Unit 204, charged with cyberpsychological warfare against enemy forces.
Capitalizing on this well-organized cyberwarfare apparatus, the North has launched a series of attacks over the last several years on South Korea’s government agencies and private firms. The magnitude of the North’s cyberattacks has increased, prompting calls for stronger measures to safeguard core national infrastructure.
“In the past, the North launched cyberattacks to show off its capabilities and presence. But things have changed. It is now focusing on developing cyberwarfare methods to steal national secrets and destroy core infrastructure,” said Kim Heung-kwang, head of the North Korean Intellectuals Solidarity group.
The cyberattack on July 7, 2009, underscored the serious impact of North Korea’s cyberterrorism. The North launched distributed denial-of-service attacks on some 35 websites of the South Korean and U.S. governments including those of Cheong Wa Dae and the White House.
Those sites temporarily went down when the DDoS attacks disabled targeted computer systems by abruptly swamping them with massive traffic.
In April 2011, the North carried out another massive attack on the banking system of the National Agricultural Cooperative Federation, paralyzing it for several weeks. The incident brought to the fore the vulnerability of the financial institutions, which are heavily reliant on computer networks.
The latest massive attack came in March 2013. The North embedded malicious codes in computer networks of three major broadcasting firms and three banks in South Korea, paralyzing some 32,000 personal computers of the firms and banks.
Seoul held Pyongyang responsible for the cyberattacks. But the North denied responsibility, saying that the South’s investigation outcomes were “outright fabrications.”
While South Korea, one of the world’s most wired nations, is increasingly vulnerable to cyberattacks, North Korea is less vulnerable given that its Internet penetration is low.
Only several hundred people in the top political echelons are known to be allowed to use the Internet provided by Star Joint Venture, a joint firm established in 2009 by the North and a Thai firm. Only a fraction of the 25 million citizens are allowed to use tightly controlled intranets.
The North also uses its own computer operating system, called “Red Star,” lessening the chances of outside attacks. But Red Star could also come under attack as it is based on the open-source operating system Linux, analysts noted.
Seoul strengthens cybersecurity Seoul established the Cyberwarfare Command, headed by a one-star general, in 2010 to deal with escalating cyberthreats from North Korea. In corps and higher-level units of each armed service, it also runs the Computer Emergency Response Team to handle any cyberintrusions.
To develop cyberwarfare experts, the Defense Ministry and Korea University established the Department of Cyber Defense in 2011. To strengthen cybersecurity policy functions, the ministry has also expanded its information protection team to create the cyberprotection policy team.
Seoul has also sought cooperation with Washington to jointly counter North Korea’s cyberthreats. In February, the allies held the first session of the Cyber Cooperation Working Group, in which they discussed joint cooperation on the sharing of intelligence on cybersecurity, development of cyberpolicies and strategies, and personnel training.
Experts say that Seoul should formulate a more comprehensive national strategy that would cover both public and military cyberissues, and promote cooperation among all related agencies during peacetime, times of crisis and wartime.
“Rather than focusing just on countering DDoS attacks, Seoul should craft a security policy that deals with the whole gamut of cyberthreats. It should have a systematic approach to detect cyberchallenges at an early date and launch quick counterattacks,” said Kim of the North Korean Intellectuals Solidarity group.
South Korea also needs to improve its military operational plans and related defense laws that focus mostly on operations in the three traditional domains of land, air and sea, said Son Tae-jong, a military research fellow at the Korea Institute for Defense Analyses.
By Song Sang-ho (
sshluck@heraldcorp.com)







![[Herald Interview] 'Trump will use tariffs as first line of defense for American manufacturing'](http://res.heraldm.com/phpwas/restmb_idxmake.php?idx=644&simg=/content/image/2024/11/26/20241126050017_0.jpg)

![[Exclusive] Hyundai Mobis eyes closer ties with BYD](http://res.heraldm.com/phpwas/restmb_idxmake.php?idx=644&simg=/content/image/2024/11/25/20241125050044_0.jpg)