North Korean state-sponsored cryptocurrency theft and money laundering have continued on a “massive scale” to generate illicit funds, while the total amount of stolen cryptocurrency jumped 40 percent just last year.
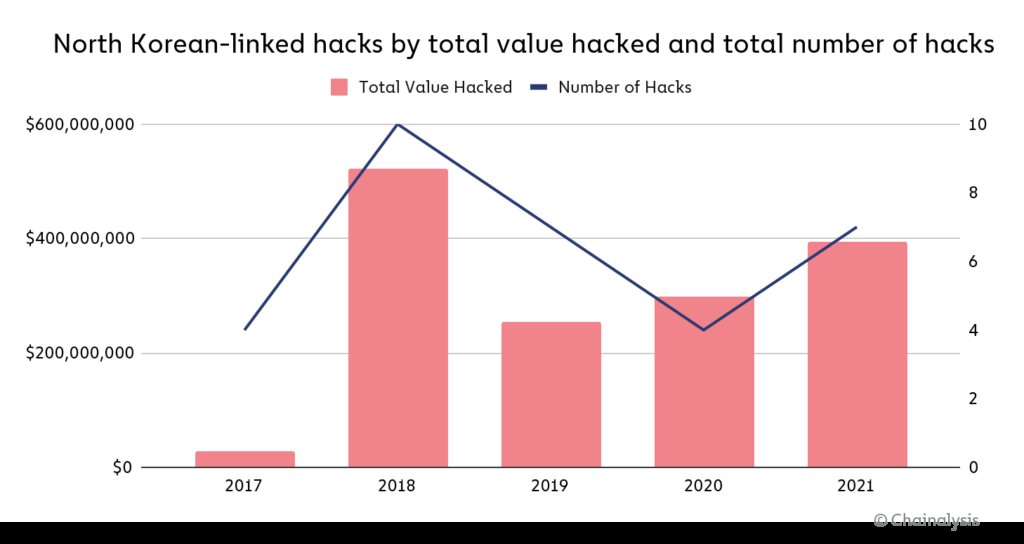
North Korea-affiliated hackers launched “at least seven attacks on cryptocurrency platforms that extracted nearly $400 million worth of digital assets last year,” Blockchain data platform Chainalysis Inc. said on Wednesday in its 2022 Crypto Crime Report.
The report shed light on a sharp increase in cryptocurrency theft by Pyongyang, which the UN Panel of Experts has pointed to as the source of illicit financing for North Korea‘s ballistic missile and nuclear programs.
“From 2020 to 2021, the number of North Korean-linked hacks jumped from four to seven, and the value extracted from these hacks grew by 40%,” the report said.
The number of hackings to steal cryptocurrency had gradually reduced between 2018 and 2020, whereas the sum total of cryptocurrency theft had risen between 2019 and 2021.
The stolen cryptocurrency is generally deposited into crypto-to-fiat exchanges and cashed out through multi-stage and sophisticated laundering processes, such as crypto swapping, mixing, and consolidation.
For instance, North Korea-linked hackers laundered roughly $91.35 million in various stolen cryptoassests after hacking a cryptocurrency exchange last August.
North Korean hackers also utilized “complex tactics and techniques” including phishing lures, code exploits, malware, and advanced social engineering to conduct cyberattacks and siphon out funds.
“These behaviors, put together, paint a portrait of a nation that supports cryptocurrency-enabled crime on a massive scale,” the report read.
“Systematic and sophisticated, North Korea’s government — be it through the Lazarus Group or its other criminal syndicates — has cemented itself as an advanced persistent threat to the cryptocurrency industry in 2021.”
Chainalysis pointed out that the US-sanctioned Lazarus Group, also known as advanced persistent threat or APT 38, is behind many of the cyberattacks primarily targeting investment firms and centralized cryptocurrency exchanges.
Lazarus Group is operated by the US and UN-sanctioned Reconnaissance General Bureau (RGB), which is North Korea’s primary intelligence bureau.
Systematic money laundererIn the report, North Korea was identified as a “systematic money launderer” which has made a “calculated attempt to obscure the origins of their ill-gotten cryptocurrencies while offramping into fiat.”
Pyongyang’s use of multiple cryptocurrency mixers was cited as the main reason. Cryptocurrency mixers are software tools that “pool and scramble cryptocurrencies from thousands of addresses” to obfuscate and conceal the flow of transactions.
In particular, Chainalysis observed a “massive increase in the use of mixers among DPRK-linked actors in 2021.”
More than 65 percent of stolen cryptoassests were laundered through mixers last year, up from 42 percent in 2020 and 21 percent in 2019, the report said.
According to the report, the trend suggests that North Korea-related actors have “taken a more cautious approach with each passing year.”
Decentralized finance (DeFi) platforms such as a decentralized exchange (DEX) were also used by North Korean-affiliated hackers for money laundering “quite a bit” last year.
But Chainalysis pointed out Pyongyang did not always rush into laundering stolen cryptocurrency into cash.
North Korea has held $170 million worth of unlaundered cryptocurrency stolen from 49 separate hacks from 2017 to 2021. The cumulative amount of their unlaundered cryptocurrency holdings hit an all-time high last year.
Also noteworthy is Pyongyang’s possession of approximately $35 million worth of cryptocurrency stolen in 2020 and 2021. It also had more than $55 million from attacks carried out in 2016, according to the report.
“Whatever the reason may be, the length of time that DPRK is willing to hold on to these funds is illuminating, because it suggests a careful plan, not a desperate and hasty one,” it stated.
By Ji Da-gyum (
dagyumji@heraldcorp.com)







![[Out of the Shadows] Seoul room clubs offer drugs to compete for clientele](http://res.heraldm.com/phpwas/restmb_idxmake.php?idx=644&simg=/content/image/2024/11/05/20241105050566_0.jpg)